Security first
At Clear Guidance Partners, everything we do is with a “security first” mindset. In today’s world, there are threats around every corner such as hackers, rogue employees and others that would love to get their hands on your data. We have built our business on establishing a high baseline of security that meets the majority of best practices, audit requirements (regulatory, client, or other) and helps you acquire and maintain the best cyber insurance. You also must be prepared for an inevitable breach, it is not possible to prevent breaches entirely, only minimizing the impact. To that end, here is a (non-comprehensive list) of the protections CGP puts in place for our clients.
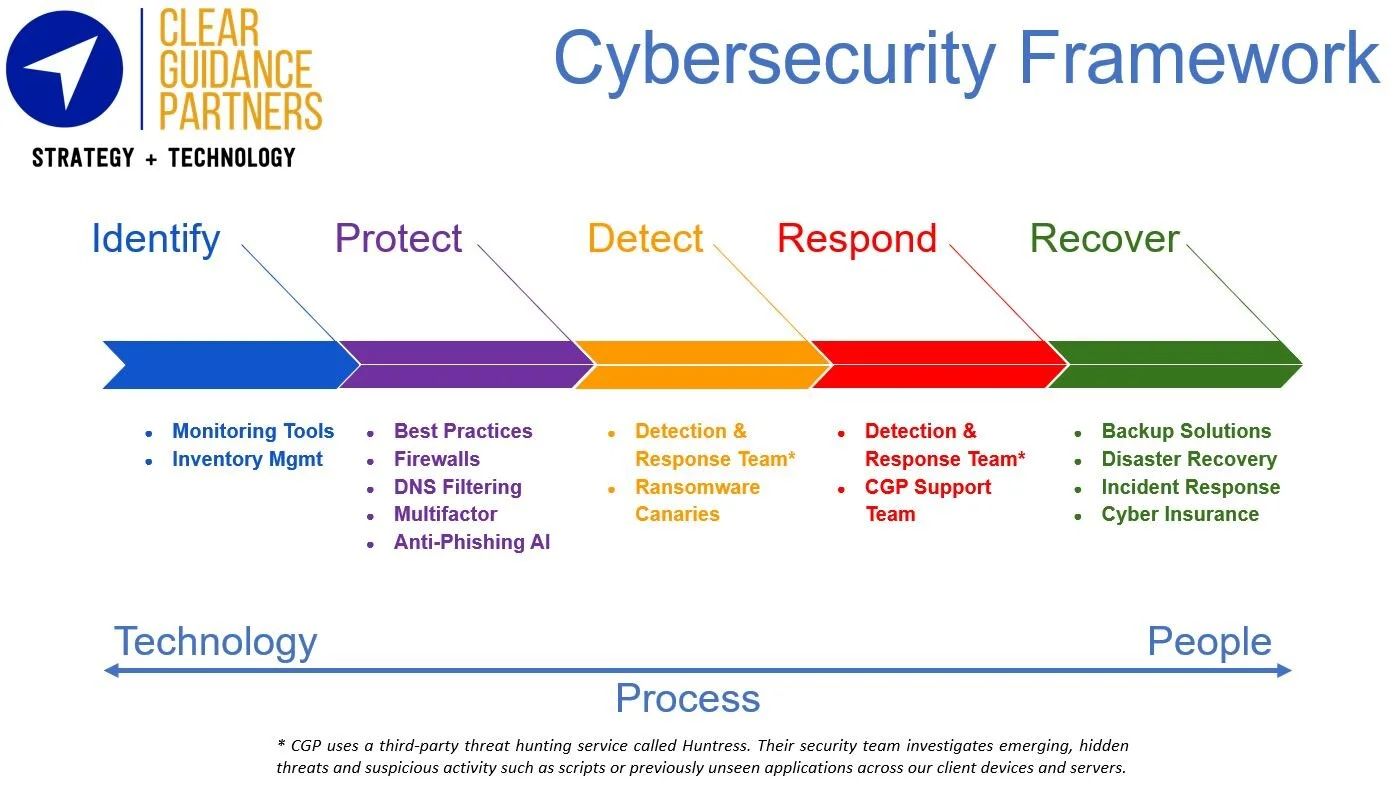
Security must operate in layers, there is no magic bullet that stops a majority of attacks. Additionally, attacks will get through, so detection and response is critical as well. CGP bases our processes off NIST CSF, a popular and nationally recognized security framework.
CGP is constantly evolving our toolset and best practices, the list below may not be current, accurate or comprehensive, and is provided for example only.
cgp internal processes
CGP maintains a $4 million professional liability & cybersecurity policy. We undergo a comprehensive, annual 114-point underwriting audit to assess our internal controls for policy renewal.
A third party security operations center (SOC) protects all CGP assets 24x7 by constantly monitoring network traffic, user activity, internet activity and more.
Multifactor authentication (MFA) everywhere
Device (ex: an app on your phone) stops 99%+ of automated attacks. CGP includes an easy to use MFA app for every user which integrates with almost any application. CGP works with each software vendor to make sure that all logins are as secure as possible.
Email protection
An edge spam filter processes every single email that comes in, blocking the majority for being blatant spam. In the event of email server/365 outages, the filter will hold incoming messages until service is restored.
Anti-phishing technology continually scans each person’s mailbox for newly discovered threats, and flags any messages that are impersonating a known contact (such as from another email address).
CGP sends quarterly (or more frequent) phishing tests to each user. Our reporting captures a list of users that click the links or attachments, and provides remedial training to prevent security lapses.
workstation / endpoint protection
CGP runs next generation antivirus and a DNS filtering service on each workstation per industry standards.
A third party threat hunting team monitors for new programs, system tasks and more, and investigates any unknown ones for suspicious behavior.
Users cannot have administrator rights to their computers due to the risk of malicious software. To help minimize headaches, a global admin rights whitelist tool is deployed. This allows CGP to allow admin rights for certain programs or installers, both on a per user and company-wide level.
Data protection
Microsoft/Office 365 does not guarantee your data integrity, and in 2020 - 2021 there were multiple high profile cases of data loss. CGP includes a third party backup service for 365.
In the event of ransomware, one standard hacker practice is to find the backups and encrypt/delete those as well. CGP puts multiple layers of protection in place for backups, separating them as much as possible from the client network using multiple encryption and segregation technologies.
policies and procedures
CGP has an extensive set of internal policies, which are also used as base templates for our clients. Our standard set of documents include retention, incident response, network use, wire transfer and more.
vendor / supply chain management
CGP keeps a set of best practices and vendor audit forms. CGP will assist with compiling a list of critical vendors (vendors holding data, vendors with access to the company network) and auditing annually.
network protection
CGP includes an enterprise-grade firewall with the full suite of security services for each office. This includes unlimited VPN users, constant web traffic scanning, and an intrusion prevention system (IPS).